Keep data safe with Google Workspace security center advanced analytics & threat intelligence tools
Security for your organization has many different aspects and components. Initially, it comes down to two things: what is your company's policy and what are the available controls? For example, the controls may enable you to prevent external sharing but it may be company policy to allow it. There are also times when the controls can’t meet the policy requirements. In these cases, additional security tools may be needed. Once your desired controls are implemented it is important to monitor and verify settings on a regular basis. The Google Workspace security health page helps you monitor existing settings and make changes based on recommendations from Google.
Once you have your policies and controls in place, the next step is to monitor and detect possible security events. Many times this process can be cumbersome and inefficient. When incidents occur it can be difficult to sift through activity logs. The security investigation tool makes this process much simpler. It gives you the power of Google search for your log data. It also integrates directly with the security dashboards, giving you built-in and custom dashboards.
Now you are monitoring and it happens, you get the alert email. A security event has occurred. It may be something simple such as an employee reported phishing. This is a good alert, a user did their part and reported phishing. However, there are some actions that still need to be taken. Immediately make sure the sender is blocked. Then determine if any other users were targeted. If so, action is needed on those messages. The security investigation tool provides the ability to quickly take log data, determine who received a message, and delete the message from all users’ mailboxes. Then you can easily create a dashboard built off of your custom search parameters.
Watch Part III of our blog series on security and privacy: Keep data safe with Google Workspace security center advanced analytics & threat intelligence tools.
Getting started with Security Center
The Google Workspace Security Center helps organizations prevent, detect, and remediate security incidents across Google Workspace. The Security Center gives administrators the ability to easily review their security health, get near real-time visibility into threats, and investigate and take action when incidents do occur.
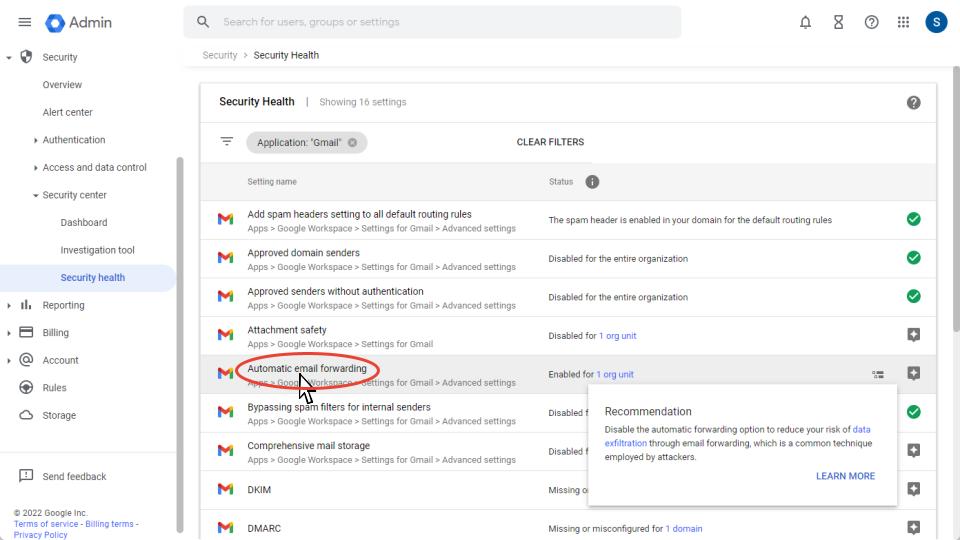
What is the Security Health Page?
The Security Health Page gives you insights into how your current environment is configured. It aggregates application settings into one location. Across each application, you can see the current status of a setting and receive recommendations on settings.
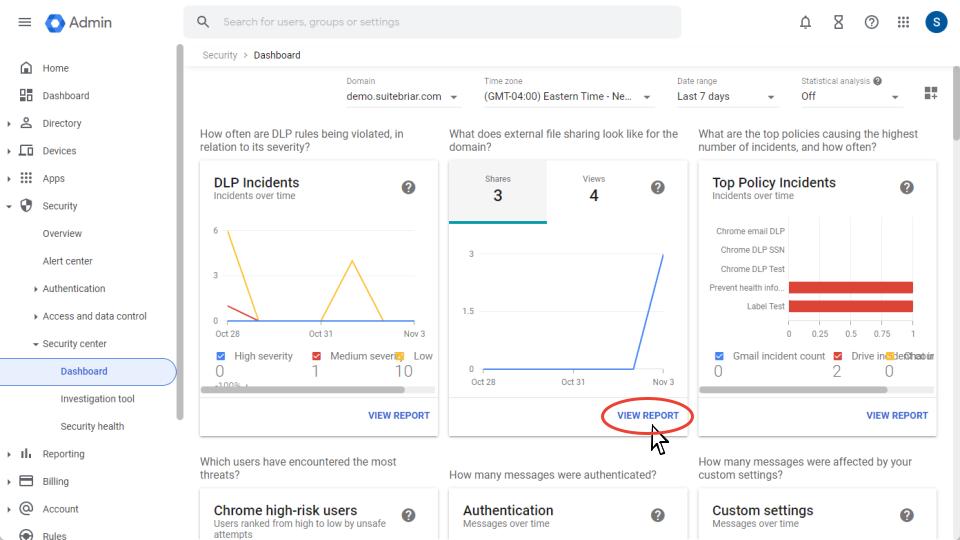
What is the Security Dashboard?
The Google Workspace Security Dashboard provides an overview of data from security center reports and custom reports. You can easily view trends over time or drill down into specific activities. The Security Dashboard seamlessly integrates with the Security Investigation Tool allowing you to pivot from dashboard data directly into a prefilled investigation.
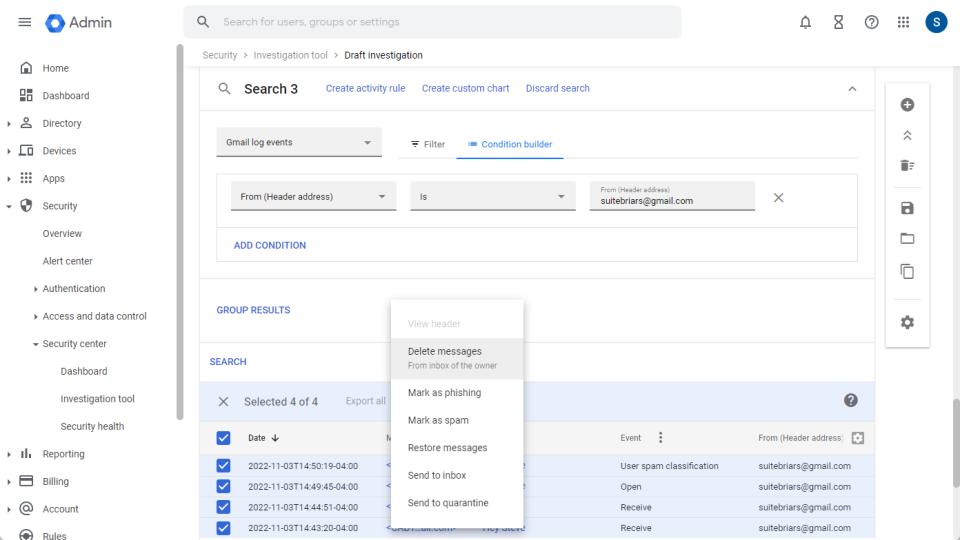
What is the Security Investigation Tool?
The Google Workspace security investigation tool can be used to identify, triage, and take action on security and privacy issues. Administrators can easily sort through data from dozens of sources. The following are some example use cases:
- Utilize Gmail log data to find and erase malicious emails
- Use Google Drive log data to investigate file sharing and modify sharing settings
- Access device logs to get an understanding of devices and applications that can access company data
In our video, we provided a high-level overview of the capabilities the security center has to offer. Without the security center, you would only have access to log data and this alone is not enough to be actionable. Log data is not helpful without the ability to easily filter data and take action. The security center helps you capitalize on the information you have available.
As a built-in feature of Google Workspace, there is no setup or exporting of logs to other systems. You immediately have access to all the available security features including the security investigation tool which our customers find extremely valuable. It helps to easily create detailed searches and update or delete the content as needed. As a Google Cloud Partner with a Specialization in Work Transformation, our seasoned team is available to help you leverage the tools within the security center to protect your organization. Schedule time with our team here.
Check back to the blog for Part IV in our Security Series: Implement Google Workspace Zero-Trust Policies with BeyondCorp Enterprise.
.png?width=125&height=125&name=Untitled%20design%20(3).png) Steve Newman Bio: I love sports and technology. I graduated from the University of Georgia where I was a member of the men’s basketball team. After college, I traveled the world playing basketball. When my basketball career was over I moved into the technology world.
Steve Newman Bio: I love sports and technology. I graduated from the University of Georgia where I was a member of the men’s basketball team. After college, I traveled the world playing basketball. When my basketball career was over I moved into the technology world.
I have worked for small early-stage startups and some of the largest companies in the world. I’ve been working in the Google Ecosystem both as a partner and as a Googler for over a decade now.



.png?width=150&height=150&name=Inc.%205000%20Annual%20List%20of%20Fastest%20Growing%20Companies%20(1).png)